Abstract
Informatization is not a new term, but it is at the basis of the information society, allowing through the continuous development of digital technologies to create new opportunities for its continuous improvement. New digital technologies of the 21st century have led to an update of the concept of informatization of society, but also revealed possible risks to privacy. In this reason, the goal of the article is to present a point of view for positive features of the informatization, its connection with globalization and relation to the basic components of the information society. A short discussion of access to information resources in the digital space with proposed formalization of the processes is made and possible risks for digital privacy which can be created by the technologies of the digital age are discussed.
Keywords: Information society, Digital technologies, Communication, Privacy, Data protection
Introduction
Informatization could be determined as a fundamental term
for building the Information Society (ISoc) just as the world
“industrialization” has been formed the name of the previous
industrial society. The term was introduced in the late 1970s by two
separate authors (Marc Port, 1977 and S. Nora & A. Minc, 1978) in
order to explain the growing importance of the information in the
society as a whole. The first official using of this term in a public
document is made in the report “Informatization of the society”,
which was been requested by Valeri Jiscar d’Esten - President of
the Republic of France. In the following years at the end of the 20th
century and the beginning of the 21st century a contribution to this
term was made by Acad. A. E. Ershov, G. Wang (1994), Everett Rogers
(2000), Kim (2004). The summary of all these discussions is related
to the application of contemporary information and communication
technologies (ICT) in different spheres of the society, as well as
to the importance of information for achieving new knowledge -
increasing the speed and quality of information services, improving
all systems through the use of computer equipment, and manage all
processes by using information technologies [1].
These aspects of the informatization set requirements for
development of an adequate policy for the functionality capabilities
of the network space, which is especially important for 5G
networks. An approach in this respect is discussed in [2] where an
Application Programming Interfaces (APIs) that enable mobile edge
applications to monitor the subscriber spending limits regardless
the way of measurement is defined. The proposed APIs permits
to increase the effectiveness of the usage of network resources by
subscribers. On the other hand, the geolocation of the resources
and users is an important part of the effectiveness of interaction
between objects in the global network. To solve this problem a
set of procedures for multivariate analysis of spatial-temporal
information and interaction in socio-economic systems is proposed
in [3] with a goal to use of intellectualization in the practice of
managing geographically related socio-economic systems.
The role of the global network in the modern stage
of informatization has led to the launch of the concept of
“internetalization” and introduction of the so-called “Internet
Governance” - use of ICT and more specifically the global network
in all processes supported by governments, the private sector,
civil society, education, technical community. UNESCO (https://
en.unesco.org/themes/internet-governance) defines it as a
central issue with the main goal to promote “sustainable human
development and building inclusive knowledge societies, and also
for enhancing the free flow of information and ideas throughout
the world”. There are clear requirements for ensuring a transparent
approach, free expression of opinions, protection of privacy
and personal data, free access to public information resources
and technical interoperability, as well as respect for linguistic and cultural diversity in cyberspace. In addition, the differences
between globalization and informatization and how this will affect
the necessary governance transformations is discussed in [4].
In this direction, the important issue of information security
in maintaining e-governance processes is raised [5], as an analysis
of the information security problems is made in the article [6].
The development of new ICT in the 21st century (Grid, cloud,
mobile cloud, Internet of Things, Cyber-physical systems, Big
data, etc.) has led to an update of the concept of informatization,
according to various modifications, but always related to access
to information resources and their application in different areas
of public relations - administration, business, industry, education,
culture, etc. This increased the requirements for understanding
the modern information processes in the society and put the
issue of information literacy on the agenda. The use of network
services, access to information and participation in e-government
processes requires a certain level of technological literacy. In the
contemporary digital era users need to know their rights to privacy
and to data protection (requirements of General Data Protection
Regulation - GDPR). In this reason, article [7] indicates that “the
process of acquiring technological literacy is costly and not trivial“
and a methodology to achieve optimality between the cost of
processes and its benefits is proposed. In addition, the authors
declare that this methodology” has a significant contribution to
protecting users’ privacy and security in the digital world”.
The main goal of this paper is to present a point of view for
the contemporary understanding of the concept of informatization
as a basis of the information society and its relation to the digital
privacy. An important task for users of information services is to
correctly determine the relationship between the benefits and the
possible negative aspects for the privacy. Indicative in this regard
is the launch the term “information avalanche”, pointing out the
advantages but also the disadvantages of this phenomenon. In
this reason, the article discusses the main characteristics of the
informatization of society and the possible problems of user’s
privacy. The paper is organized as follows. Section 2 deals with
the features of the informatization and it role in the development
of the contemporary digital society. Section 3 discuses shortly the
possibilities for access to information resources and proposes a
formal description of communication in the digital space. Section
4 presents a point of view for possible problems for digital privacy
which can be created by the technologies of the digital age.
Informatization as a Basis of the Information Society
Features of the Informatization
Informatization of the society is a technological, socialeconomic
and cultural process leading to important changes of the
individual’s life, requiring significant efforts of the government,
business and all users of ICT to form adequate information culture. Two basic theoretical-methodical approaches to informatization
could be defined:
a. Technological approach that is mainly associated with
developing technical and technological means and tools
to support labor activity in the field of manufacturing and
management to increase efficiency and productivity.
b. Sociological approach, which considers informatization
as an impact on all spheres of the human activity with reflection
to the all persons in the society - their knowledge, skills, moral,
economic and culture interests, personal development, etc.
The following basic technically & technological components of the informatization can be defined
Electronization: dissemination electronic technologies in different fields of the human activity: manufacturing, management, education, research, social and cultural spheres, etc. Often this component of informatization is associated with digitalization, as done in the article [8] where is stated that “… informatization, digitalization (electronization) of the economy and the widespread introduction of ICT creates the basis for the movement of all countries of the world to the information society…” and adds that the global information space provides free access to different information resources and electronic interaction between people. The article states that electronization is an important factor for improving the efficiency of the digital economy of each country. The essential role of electronization in the contemporary society is confirmed in [9], pointing out that the process of electronization is one of the milestones in the development of the society.
Mediatization: a process of improving the means for collecting, storing and disseminating information, for which electronic (digital) media are mainly used, in order to speed up the transmission of information and increase the possibilities for the ways of this transmission. Jan van Dijk defines the current communication revolution with network society and determines as its main part the digital media [10]. Four structural characteristics of the digital media are defined - integration, interaction, digital code, and hypertext. A critical review of the mediatization theory is made in [11] where two forms are discussed - a strong form in which “media logic” determines the actions of different social institutions and groups, and a weak form, which, despite the recognition of the role of the media in social life, denies the existence of such logic.
Computerization: process of improving the ways of searching and processing information through the use of computer means, in which the computer becomes the main means of communication of people and their release from routine operations. This component is typical for the information society and most important task of all spheres of human activities, as stated in [12]. The article makes a direct connection between computerization and individual professionalization in information society, defining the second term as “a process of professional growth and professional training, i.e. professional self-realization is a form of self-actualization”. On the other hand, the authors define computerization in the information society as informatization of all forms of professional development and wide introduction of information technologies in the individual professionalization.
Intellectualization: process of development of human knowledge and possibilities for creation of new information, which naturally increases the intellectual potential of the society, including opportunity to use artificial intelligence. A point of view for the role of intellectualization in the contemporary information society used for managing distributed socio-economic system is presented in [3]. Discussion of the intellectualization as one of the main challenges of modern ISoc is presented in [13] as a form for extracting knowledge from an increasing information flow and composition of algorithms as a means of intellectualizing of knowledge is proposed.
Informatization and Globalization: An interesting point of view on the nature and difference between the concepts “informatization” and “globalization” is presented in the article [4]. The advantages of modern cyberspace based on electronics, informatics and telecommunication technologies are recognized, which provides a completely new approach of society to the management and exchange of data, including the control of real systems. Against this background, the question arises about the difference between “informatization” and “digitalization”, considered as two different approaches for transformation of the social system. Preference is given to informatization as the basis for the development of the digital age.
It is emphasized that the replacement of the generation of terms such as “e-” / “electronic” or “digital” with “new” modern words starting with “smart-”, “intelligent”, “Cyber-physical”, “-4.0” (from “Industry 4.0”) does not lead to clear terminology in technological terms and is justified by the term digitalization. Particularly telling in this regard is the term “Industry 4.0”, which describes a future vision for the industry until 2025, based on modern digital technologies such as cloud / mobile cloud computing, Internet of Things (IoT), Cyber-physical systems (CPS), big data analysis (BDA). etc., with the basic idea that all this would lead to a fourth industrial revolution.
All this gives grounds to explain the difference between digitalization and informatization, considered as technologies for managing activities in the modern digital space. Based on technological development over the years computerization and digitalization are defined in the article as the third generation of social development, as the the informatization as determined the next fourth generation, justifying the new in it by “reliance on the digital (computer) file as the descriptor of a system’s (or digital object’s, respectively) characteristics and state”. And it is clarified that, unlike the long-known computer file, the new type allows embedding, sharing and editing in the network space.
Informatization and Information Society: The combination of the presented components of informatization allows to create an adequate basis for the development of the information society as a set of modern ICT, means and tools for information processing to obtain new knowledge to help people. Electronization and computerization, together with network technologies, help to create the necessary global infrastructure as a media for access, transmission and dissemination of information, which be used for intellectualization of all activities. The result is defining the global goal of IS in the following three directions:
i. in the public sphere - creating conditions for citizens for effective electronic information service (e-servicing) while ensuring their rights to knowledge, information and protection;
ii. in the sphere of industry - providing complex automation for all branches of material production;
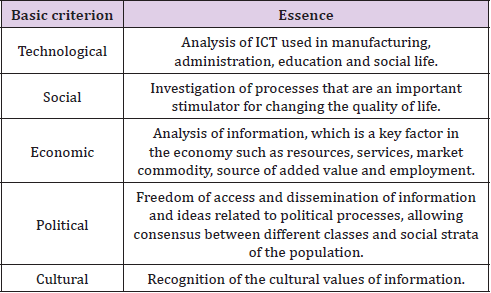
iii. in the scientific field - ensuring the continuous development of science in order to ensure the scientific substantiation of the emerging problems in the informatization of society. The level of maturity of the IS could be evaluated on the base of the criteria presented in Table 1.
The following basic elements of ISoc can be identified:
i. ICT (Information and Communication Technologies) -
a set of computer equipment, software, computer networks
for data transmission and the created local and distributed
information systems with databases.
ii. Information resources - information and related technical
equipment, software, description data and information objects
that are designed, built, developed and managed to maintain
information services.
iii. Information security - measures and procedures to ensure
an acceptable level of protection of information resources from
accidental or intentional actions such as disclosure, alteration
or destruction.
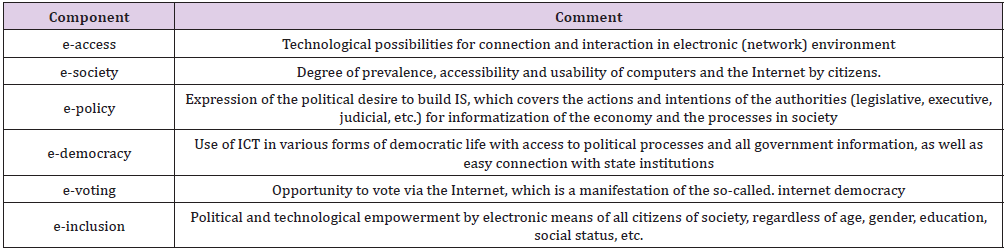
The contemporary information society is presented with a large number of components, and in addition to the traditional and strongly embedded in public life, such as e-health, e-governance/egovernment, e-learning/e-education, e-business/e-commerce (with related e-pay and e-banking), can be defined others some of which are summarized in Table 2. To the listed components can be added other such as e-parliament, e-justice, e-legislation, e-referendum, e-campaigning, e-consultation, e-petitioning, e-polling, e-mediation, etc. The contemporary level of informatization in the digital age gives rise to various concepts starting with “e-”.
Formlization of Processes in Digital Space
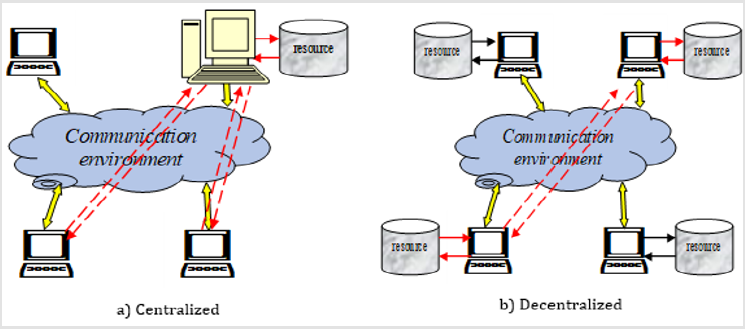
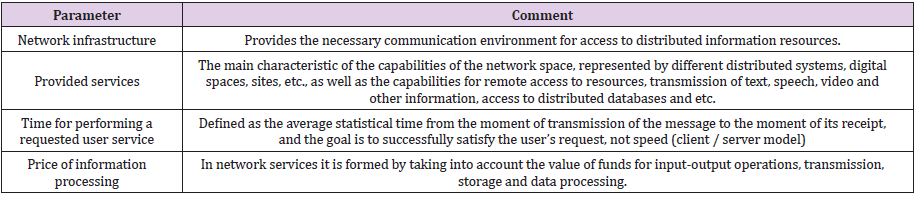
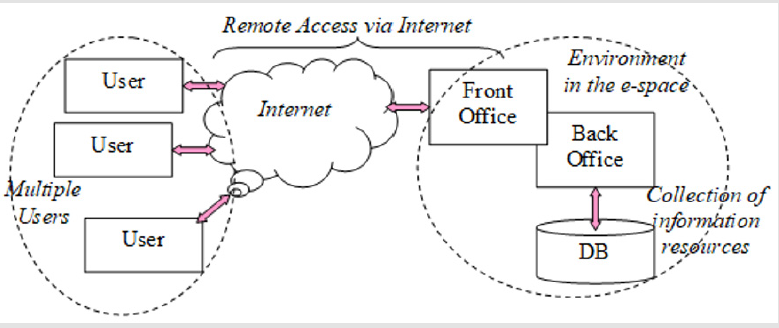
All information resources should be considered as integrated information (structured data) supported by technical and technological means (computer equipment, software, meta-data for description, tools for design, development and management, etc.). There are two main ways to store and process information in the network space (Figure 1) - centralized (concentrated in one main computer with remote access of users to it through a communication environment) and decentralized (resources distributed on different computers with communication between their management systems). In both cases, distributed access to information must be subject to an Information Security Policy and strict control for the protection of user personal data (Data Protection) and privacy. To assess the effectiveness of the digital age and their infrastructure in accessing and using information, basic parameters summarized in Table 3 are applied.
Digital space can be considered as a set of independent territorially remote units with their own internal structure and functionality (Figure 2), which allows formalization through a directed graph with a discrete set of nodesV ={Vi; i = 1 ÷ n}, entering into relations with each other, represented by connecting edges of the set A = { aij: Vi → Vj }. Each relation between pairs of independent nodes is represented by a weighting coefficient dij, corresponding to the communication parameters between the individual localizations of the objects.
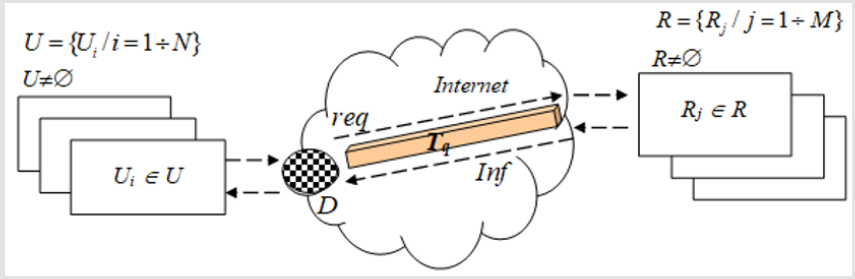
Formal, the nodes in the set V can be divided into two relatively independent subsets U (users area) and R (resources localization) supported by two additional sets to maintain and manage the transmission of the communication units - requests (req) and provided information (Inf). The formal definitions of all components is presented below (Figure 3).
a. R = { Ri/ j = 1....M}, T ≠ ∅ - Users providing multiple remote access to one or more units in the digital space by request req: Ui ∈V ;
b. D = { DIN, DOUT} R ≠ ∅- Resources, which are subject to remote access, providing digital content Inf:Ri → Ui;3a∀Ui∈Uℵ∀Rj ∈R ;
c.T = { Tq/q= 1....K } T ≠ ∅- Transmitters of communication medium for transfer of information objects;
d. D = { DIN, DOUT} - Distributors of information objects (protocols, means, tolls, etc.) for distributing communications between U and R.
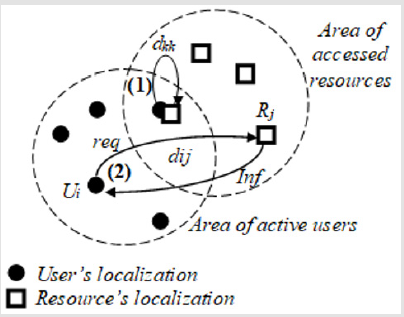
The communication distance between the active participants - nodes of V with users Ui ∈ V and resources Rj ∈ V is represented by the communication parameters dij ( i ≠ j; i, j∈ {1 ÷ n}). In case a user Ui accesses an information resource Ri in the same node is accepted dii = 0. On this basis, a matrix of communication distances DM = {dij} with dimension n = ||V|| with zero parameters on the main diagonal is constructed, allowing determination of the minimum paths between independent nodes in the structure (Figure 4).
The actual localization of the components in the individual physical nodes of V is important for the specification of the processes in information services. For the general situation, it is assumed that and one or more nodes of V can contain objects from both groups (the sets U and R). This allows the formation of two types of relations
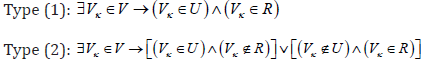
To determine the affiliation of a node to a given type, two binary parameters {0,1} uik ∈ and {0,1} rjk ∈ are defined, corresponding to the actual localizations of user Ui∈ U and/or resource Rj∈R in a given node Vk∈V. Based on the actual localization of the active objects, two localization matrices UL = {ujk} and RL = {rjk} can be constructed, through which they could be defined a new vector VL by the procedure below according to which elements VL[κ ] =1 determine the existence of a relation of type 1, and in case VL[κ ] = 0 the relation is of type 2.
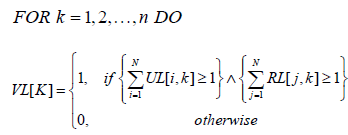
Formalization allows to conduct a deterministic study of processes in digital space by establishing binary relations between active nodes, and each transaction can be described by an ordered pair (u, r), where u∈U and r∈R .
Informatization and Digital Privacy
Various features and characteristics of the contemporary digital age can be defined. For example, the definition “Network society” is proposed in [10], which is based on the role of the global network in social and industrial life. In addition, some basic characteristics are defined to support it - social equality, quantity & quality of social relationships, democracy & freedom, riches of human mind. An exemplary summary of the functional characteristics of the digital age discussed in the information space can be made as follows.
a. Knowledge orientation (knowledge is the main production
and main priority),
b. Digital form for presentation of objects (digitization of
documents and document flow),
c. Virtual nature (virtualization of the real physical
environment through the application of virtual data and
systems for “virtual reality”),
d. Extensive functionality (components for multiple and
multifunctional use are created),
e. Integration and interconnections (construction of
a unified universal network infrastructure from separate
independent modules for services and manufacturing),
f. Dynamic operation (implementation of activities in real
time with access to all necessary components),
g. Global scale (globalization of knowledge and opportunity
to implement activities from different places).
All this diversity of functionalities of the digital age generates massive information flows distributed between the global networks nodes. The dissemination of information in the digital age is significant and it is not in vain that there is talk of an “information avalanche”, but this abundance in the global space can have undesirable effects, such as:
a. Devaluation of information,
b. Obtaining poor quality knowledge,
c. Spending too much time and attention by users to “surf”
the web,
d. Loss of productivity due to spam,
e. Additional costs related to data transfer, storage options,
etc.
f. Security and privacy issues (last but not least).
In this context, it is necessary to be discussed the important
question “How does informatization affects the privacy of users
of digital services in the network space?”. This is essential for
cloud technologies, IoT, smart technologies, big data, etc. It is not
in vain that the latest legal documents in the field of personal data
protection (for example GDPR) raise the issue of digital privacy of users and set specific requirements related to the right to privacy
and the right to data protection. Contemporary technologies of the
digital age generate their specific challenges to digital privacy [14],
which requires adequate measures for secure access and legitimate
use of information resources, including personal data sets [15].
The result of the rapid informatization of society is its growing
dependence on the network space and the digital services provided
in it, which increases the risk of violating information security and
privacy.
Examples of research in this area related to the possible risk to
information security in cloud infrastructure and the principles of its
management are presented in [16,17]. There is also a risk of privacy
with technological solutions using multiple points (sensors) for
access to data (Internet of Things), “smart” technologies for home,
city, transport, etc. (Cyber-physical systems), accumulation of big
data and their processing [18]. A summary of the main risks for
users in the digital age is presented below.
Digital Space
Any information published in the network space must be correct, reliable and the necessary measures must be taken to protect it. The risk of non-compliance with these requirements is the creation of opportunities for financial and psychological consequences, as well as consequences for reputation. The information disseminated in the global network must comply with the requirements for legal and correct processing of personal data, the information must be sufficient and relevant to the goal, to have the consent of the person. In case of incorrect information or at the end of the set goal it is necessary to observe the paradigm “the right to be forgotten” - the right of the subject of personal data incorrect data to be corrected, removed or blocked. When maintaining mobile communications and those in the global network, service providers must ensure the necessary level of confidentiality, caller identification, anonymization of traffic and location data, and ensure the security of the services offered.
Social Computing
Many social applications collect personal data outside the main
purpose, which requires a serious risk analysis in their privacy
policy. Examples of risk are the following:
a. The amount of information collected during registration
or profile update (names, address, date of birth, telephone or
fax number, e-mail address, publication of materials, other
publicly available information, information from another social
media),
b. Information about correspondence with the site
administrator,
c. Details of visits (date and time of access, pages viewed, IP
address, type of browser, hardware and software used, traffic
data, location data, blog and other communication data and resources used),
d. Location data when accessed via a mobile device and
information about these devices (identification number and
type of device),
e. It is not clear who owns the data published on social
media and whether complete deletion of profile data (and
copies) is guaranteed at the end of the participation.
Cloud Computing
The main feature of cloud services is that the resources are
outside the client’s security side, which imposes the requirement
to know what security practices are applied and whether privacy
regulations are followed. Some of the possible risks are the
following:
a. Violation of the confidentiality of information when many
users have access to the cloud space,
b. The share link approach is convenient for sharing data
with business partners, but creates preconditions for a breach
in system security and data leakage to an unauthorized domain,
c. Multiple hiring in the cloud can create a risk of breaching
the integrity and availability of supported data (unauthorized
deletion, modification, theft),
d. Presence of residual data (“forgotten” copies) when
deleting or removing data in the cloud,
e. Confidentiality of the software to ensure reliable
processing and counteraction against unauthorized (intentional
or unintentional) integrity violation.
Internet of Things (IoT)
Confidentiality in IoT is one of the specific considerations for ensuring reliable protection of personal data, because almost every physical or logical object or object can receive a unique identifier and ability to communicate freely over the Internet or other network. Endpoint data cannot in itself lead to privacy issues. The problem is that when even fragmented data from multiple endpoints is collected, compared, and analyzed, they can provide sensitive information. IoT security is also an issue because the plurality of Internet devices and various computers involved are often configured with standard or weak passwords, are not securely protected, and objects (things) can be used as separate objects of attack. The main security risks with IoT are the following:
a. Insecure web interface,
b. Inappropriate authentication and authorization,
c. Insecure network services,
d. Lack of encryption during transfer,
e. Secure cloud and mobile interface,
f. Unreliable security system configuration and unreliable firmware,
g. Poor physical security
Big Data
Big Data is collected and stored information in very large volumes, received from various sources, intended for further processing for some purpose. The idea of “the more data, the better” is a major problem for information security and privacy, because data is collected from many different sources, as well as from different forms of existence.
Big Data Analytics: Big Data Analysis is a method for analyzing big data to reveal the causes of events, study trends and form forecasts. The results can lead to privacy issues:
a. It is possible that multiple pieces of data may contain
assets that are subject to security breaches,
b. Technology makes the principle of “data minimization”
meaningless,
c. The data may have been initially collected for another
purpose,
d. Violation of anonymity in collecting so much data and use
of powerful analyzes, as well as violation of the requirement
for transparency of the applied methods of personal data
processing.
Conclusion
Informatization creates the necessary basis for the development
of the information society and the application of modern
technologies for the benefit of the people. Their important role in the
development of industry, public life and all accompanying practices
related to access and processing of information to generate new
knowledge cannot be denied. Informatization inevitably leads to
the intellectualization of society and increase personal confidence
in the performed activities. In today’s digital age, personal data is
becoming an important resource for organizations, institutions
and service providers, including the analysis of consumer behavior.
Quite often users themselves share their personal data and details
of their personal life in the network space, especially on social
media.
This creates an opportunity for incorrect speculation with
accessed personal data and their use for commercial purposes.
It is no secret that business organizations collect preliminary
information about job applicants, the behavior of their employees,
their financial and behavioral ratings. Data collection is also a
task of supported websites for self-presentation, for contact with
potential customers, for research of consumer interests, etc. On
the other hand, when using digital communications and services
in the network space is not always monitored to provide personal
information in the minimum required amounts.
Users need to be aware not only of the opportunities and strengths of global informatization, but also of the potential risks to their privacy and their personal data. Defining specific legal requirements for the digital space only will not lead to a positive effect if the digital literacy of the society for the special features of the modern digital age in the field of informatization, technologies, security and privacy is not constantly increased.
References
- IGI Global. What is Informatization.
- Atanasov I, E Pencheva, A Nametkov, V Trifonov (2019) Functionality of policy control at the network edge. International Journal on Information Technologies and Security 11: 3-24.
- Goryachko VV, ON Choporov, AP Preobrazhenskiy, OJ Kravets (2020) The use of intellectualization management decision-making in the interaction of territorially connected systems. International Journal on Information Technologies and Security 12: 87-98.
- Paulin A (2018) Digitalization vs. Informatization: Different approaches to governance transformation. CEE e|Dem and e| Gov Days pp. 251-262.
- Schinagl S, Shahim A (2020). What do we know about information security governance? “From the basement to the boardroom”: towards digital security governance. Information and Computer Security 28: 261-292.
- Aidinyan AR, OL Tsvetkova, AN Gerasimenko, O Ja Kravets (2020) The analysis of information security problems solved by clustering methods. Journal of Physics: Conference Series 1679: 022084.
- Hirschprung RS, S Tayro, E Reznik (2020) Optimising technological literacy acquirement to protect privacy and security. Behaviour & Information Technology.
- Kuzovkova T, D Kuzovkov, O Sharavova (2020) Transformation of criteria and indicators of digital development of economy and information society. Proceeding of the 24th Conference of Fruct Association, ISSN 2305-7254, pp. 682-687.
- Stofkova KR, J Stofkova (2020) Use of Open Data in the Development of the Digital Economy in the Knowledge Society in the Era of Globalization. SHS Web Conf. article 03008, 10 Jan 2000, The 19th International Scientific Conference Globalization and its Socio-Economic Consequences 2019 - Sustainability in the Global-Knowledge Economy 74.
- Van Dijk, Jan (2020) The network society, (4th). SAGE Publication Ltd. London, UK.
- Ampuja M, J Koivisto, E Väliverronen (2020) Strong and Weak Forms of Mediatization Theory. A Critical Review, Nordicom Review 35: 1.
- Tsvyk VA, IV Tsvyk (2018) Individual professionalization in information society: challenges and prospects. RUDN Journal of Sociology 18: 418-430.
- Vatian A, S Dudorov, N Dobrenko, A Mairovich, M Osipov, et al. (2019) Intellectualization of knowledge acquisition of academic texts as an answer to challenges of modern information society. In: Chugunov A., Misnikov Y, Roshchin E, Trutnev D (eds) Electronic Governance and Open Society: Challenges in Eurasia. EGOSE 2018. Communications in Computer and Information Science (book series), Springer, Cham, 947.
- Romansky R, I Noninska (2020) Challenges of the Digital Age for Privacy and Personal Data Protection. Mathematical Biosciences and Engineering. AIMS Pres 17(5): 5288-5303.
- Romansky R, I Noninska (2018) Principles of Secure Access and Privacy in Combined E-Learnng Environment: Architecture, Formalization and Modelling. Chapter 9 in the book: “Multidisciplinary Perspectives on Human Capital and Information Technology Professionals” Vandana Ahuja & Shubhangini Rathore (Eds.). IGI Global Publ., USA, ISBN13: 9781522552970; EISBN13: 9781522552987, pp.152-178.
- Tsaregorodtsev, Anatoly V, Oleg Ja Kravets, Oleg N Choporov, Anna N Zelenina (2018) Information Security Risk Estimation for Cloud Infrastructure. International Journal on Information Technologies and Security 10(4): 67-76.
- Tsaregorodtsev AV, MS Shikhaliev, I Ya Lvovich, AN Zelenina, ON Choporov (2019) Information Security Management for Cloud Infrastructure. International Journal on Information Technologies and Security 11(3): 91-100.
- Ivanova D, A Elenkov (2019) Big Data Analytics for Air Quality Monitoring Assessment Based on IoT Platform. International Journal on Information Technologies and Security 11(2): 43-50.

 Review Article
Review Article