Abstract
Social interaction is a key feature of human society, and in today’s digital world this is facilitated by new technological possibilities. Social communications are even more important in the context of the COVID-19 pandemic, but they must consider the need to protect personal data and counteract the possible risk of privacy breaches. This requires a good level of digital literacy of users, which in the modern information society is associated with knowledge of the technological features of network processes and the need to ensure information security of own personal data and proposed information materials. The article discusses the role and place of social computing in the modern information society, including by highlighting the main forms of conduct, features, advantages, and disadvantages. The main attention is paid to the personal inviolability of the participant’s personal life (privacy) in social communications and the need to protect personal data and personal space.
Keywords: Informatization; Digital Technologies; Social Communications; Personal Data; Privacy
Abbreviations: ICT: Information and Communication Technologies; CI: Collective Intelligence; SoC: Social Computing; SNS: Social Networking Sites; GDPR: General Data Protection Regulation
Introduction
Communications are directly related to human activity and are inherent in the mental characteristics of human associations. They directly affect the personal space of each individual because the presence of only one person in the observable individual area of the personality leads to the stimulation of social communication [1]. The term “communication” is of Latin origin and combines activities between individuals such as communication, conversation, connection. With the entry of informatization [2] in the social life of society, the term acquires a modern meaning related to network technologies and the implementation of communications in the global network space. This allows interpretation in the direction of communication between people through means of communication of material and intellectual nature and sharing information between them in social communications. In addition, the meaning of the term “social” can be considered, referring mainly to the life of individuals in society (social status) and communication between them (social contacts). This allows us to make the following summary [1]: “Communication is a set of processes that take place in and between social communities and consist of the exchange of information, interactions and mutual perception and understanding.” Social communication is seen as a process involving a series of interactions between elements that result in a new product from the primary material that is transformed but none of it is eliminated.
These interactions encourage communication by transmitting information in explicit or implicit form. Implicit signal sharing activates neural mechanisms in individuals, which can lead to changes in their internal state. A study in this direction was presented in [3], where based on a model of neural chains in rodents, a connection with humans and the social interactions between them modified by the COVID-19 pandemic was made. The global health crisis caused by COVID-19 and the need for a significant change in the behavior and communication of individuals is discussed in [4], where the need for social and behavioral sciences to help adapt human behavior to anti-epidemic measures and requirements. Specific research topics are defined for the impact of social and cultural influence on behavior, threat identification and scientific communication in research, which must be conducted as soon as possible. The article discusses the role and place of social computing in the contemporary information society, including in the time of the COVOD-19 pandemic, highlighting the main forms of implementation, features, advantages, and disadvantages. In this aspect, the main attention is paid to the personal inviolability of the participants in social computing and the need to protect personal information.
In the next section 2 some features and concepts in the field are discussed, as in section 3 an exemplary classification of the environments for social interactions is made. The main topic of the impact of social computing on privacy is discussed in section 4, and the main possibilities for violation of principles for personal data protection and user’s privacy are systematized.
Social Computing
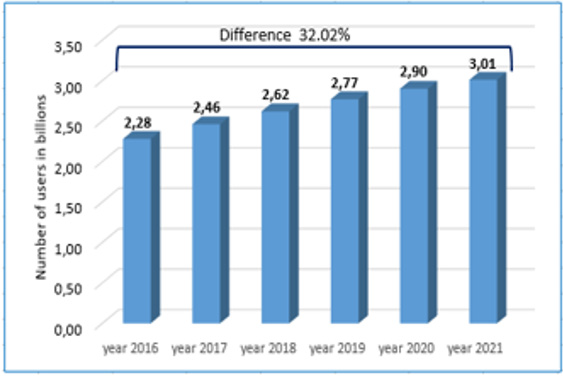
The quality and availability of devices with Internet access have increased significantly in recent years, which has also affected access to various sites. The relative part of access through a mobile operator and via a tablet is increasing. This determines the relatively constant increase in the number of social media users worldwide (Figure 1), as for the period after 2016 an average annual increase of 5.86% can be calculated, and for the presented period an increase of 32.02%. The Internet offers tools and opportunities for organizing social communication between individuals through modern information and communication technologies (ICT). This makes social communications a global phenomenon with a great variety of users’ locations, and their use can be analyzed in a number of ways, introducing the following basic concepts.
Figure 1: Statistics on the growth of social media users (according to forecast data from Statista).
Social Web
A community of interconnected people who interact through conversations or participation with content over the Internet, creating various web applications [5,6]. Users often interact to discuss, use, and share web services posted by other users. This determines the need for timely discovery of web services, which can be done by applying effective search engines based on keywords and information retrieval techniques. A solution to the problem is given in [5], where it is stated that traditional techniques have limited capabilities and suggests the use of the so-called. ‘Variational Auto coders’, which are deep neural networks used to study effective codes. On the other hand, it should be noted that the generation of a large amount of information (the so-called “information avalanche”) reduces its reliability and leads to a risk of misinformation, which requires adequate measures to regulate it [6].
Collective Intelligence
(CI) is a collection of Internet users who gather and share content to create something new that is impossible for a person. This approach is evolving significantly with the dissemination of new technologies for accessing, processing, and sharing knowledge, providing resources for training, decision making and forecasting for the development of processes and situations. This requires the development of appropriate models for solving emerging problems, and in this respect, a systematic review of the frameworks for the development of CI (proposed in the scientific literature after year 2000) is made in [7]. As a result of this study, a summary of available knowledge has been made, and based on several popular CI initiatives in the global network, a new model for describing CI systems with clearer presentation of the various components has been proposed. On the other hand, in solving problem situations and making management decisions, the correct formulation of the set task is essential, as the “phenomenon of problem formulation” is discussed in detail in [8].
Social Computing
(SoC) is a collaborative interactive aspect of online behavior created as a result of the development of Internet communications and the ability to exchange different types of information. It covers activities in the global network in which users are not only passive participants, but also implement various forms of direct communication, information sharing and opening their own profiles. Globally, SoC should be seen as a complex of different web-based and mobile technologies, allowing the transformation of traditional communication into an interactive dialogue by sharing photos, images, audio, video, experience, etc., as well as creating, editing and distribution of content on the Internet, accessible by different people located in different places. One example of the application of the SoC is the development of environments for access to cultural heritage, oriented to socially isolated people with special needs [9]. The article reviews publications in this area of SoC, summarizing basic technologies and presents examples of innovative approaches to interaction with users. An important feature of the publication is the discussion of the requirements for ethical considerations in the design of such environments and counteraction to opportunities for breach of privacy.
The main representatives of social computing are social media, social networks, websites for sharing video content (YouTube, VBOX7, Flickr), Internet forums, wiki applications, virtual social media (Second Life), virtual gaming sites (World of Warcraft), etc. The main use of the term “social computing” is as a reference to the above environments for social interaction, and in [10] it is proposed to expand this concept to cover the extended range of dynamic social interactions and calculations related to interaction of the social sciences with computer science. It is emphasized that the ever-increasing avalanche of social information, the development of modern computer technology with capabilities for collective intelligence, innovation in network communications and the growing complexity of interactions in the network world, require the development of a new vision for social computing. It must formulate clear rules and trends for intellectual communication “human-computer” in order to form a unified common set of tools for generating knowledge, forming collective intelligence, and providing social benefits. On the other hand, the time for realization of the various activities in SoC is essential. In this regard, an algorithm for estimating the time of posting messages in online social networks communities is proposed in [11]. When estimating the time, characteristics such as participating users and sent messages are analyzed, in order to determine the best rating.
Classification of Social Computing Environments
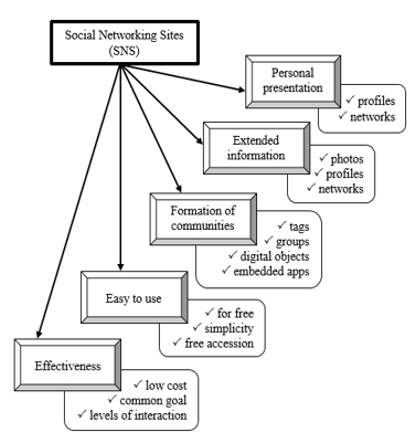
Social computing (SoC) is an interactive and collaborative behavior between users in the global computer and network space. When working independently with a personal computer, the user determines his own behavior and the activity of the computer equipment. With SoC, the Internet allows users to interact through a variety of environments organized on Social Networking Sites (SNS), including a variety of social media environments. The main components, features and characteristics are presented in (Figure 2).
Theoretical research should answer the following questions:
1. What are the main problems related to SoC? Is it possible
to identify problems that are common enough for a wide range
of social applications, but at the same time related to real
situations?
2. What are the right models? The literature increasingly
argues that human online behavior often deviates from
standard economic patterns of behavior, and this may indicate
an impact on optimal system design. As mentioned above
[7,10], a dialogue between theoretical and empirical research
is needed to define appropriate models.
3. How should success be measured? Assessing
developments in the field of SoC in general, the criteria for
success are unclear, because the capabilities and use of these
systems are constantly changing.
Depending on the specific application and their purpose in
social interactions, SoC environments can be differentiated in the
areas presented below.
Social Media
websites that are filled with content by users. The user decides which information to publish; blogs can also be defined as social media (Wikipedia, Scholarpedia, Google-encyclopedia Digg, Mixx, Stuble Upon, e-Britanica, etc.). The term is a summary of environment for social interaction which are created and used for communication, sharing personal photos, files or media content, turning communication into an interactive dialogue. They have different forms depending on the shared information (text, images, video and audio, etc.) or depending on the organization of communication (direct dialogue - chat, article sharing, music sharing, blogs and micro-blogs, virtual sites and etc.).
Social Networks
Other than social media because the main goal is to create, store and maintain information resources for continuous contacts and long-term usability (Google+, Facebook, LinkedIn, Pinterest, Twitter, Instagram, Friendster, MySpace, Black Planet, Ning, Xing, GPlus , Vine, Tumblr, etc.). The aim is to create a social structure of individuals (or organizations) connected in network-specific types of relationships such as friendship (kinship), ideas, views, traditions, financial relationships, hyperlinks, etc. To represent the relationships in a social network, the terms nodes (individual participants or organizations) and connections (lines of social connectivity) are used, which allows the construction of a diagram to represent the topology of connectivity, most often through a nonoriented graph.
Social Bookmark
A collection of sites where users post links to resources for next (and reusable) use by organizing, storing, managing, and searching for bookmarked resources online. This is a method that allows users to create and apply tags to the information content they want to retrieve at a later stage. Unlike file sharing, the resources themselves are not shared, only the bookmarks that mark them. To increase search efficiency, metadata can be added, which can be freely selected keywords, comments, votes (“for” / “against”), etc. These labels can be organized, managed, indexed, and shared with others for later retrieval of content (also called co-tagging, social indexing, and social marking).
Social Aggregators
A “social” group of sites that collect user activities related to the above categories of SoC. This form of social contacts allows the exchange of information and comments, voting on a case, cooperation, etc. Aggregation platforms allow participants of different social networks to share real-time information with each other, which eliminates the need to switch from one to another social network or media.
Impact of Social Computing on Privacy
Despite the significant advantages of SoC for social interactions, the possibility of accidental or intentional intrusion into personal space must also be considered, which may be provoked by the user himself. According to the opinion expressed in [6] (see above), there is a risk of misinformation in the generation and dissemination of social information due to the absence of trusted intermediaries. Unfortunately, this is largely related to the required level of digital literacy of users, not only in social contacts, but in general in the use of contemporary digital services. The danger of false information is one side, but it must be complemented by risks of privacy and speculation with personal data available in the network space. On the first side of the problem, models have been developed for detecting misinformation using machine learning techniques and artificial intelligence. The review of research conducted to solve problems of this type presented in [6] discusses approaches in tree main areas - detection of unwanted opinions in the review sites; detecting fake news on microblogs; assessment of the reliability and correctness of online health information. In addition to the above, the possible risks when using SoC by the business can be added, related to the use of sites for advertising company products, possible negative comments from users about it, “nagging” with company activities, etc.
About 35% of employers admit that they use data from social networks for their own purposes - market investigation, selection of new employees for appointment, evaluation of their employees, etc. To this must be added the opportunities for violation of information security, intellectual property and copyright, leakage of personal data of employees or corporate strategic information, unreasonable and bad content generated by customers, cybercrime and cyberbullying of employees. The second more significant side of the problem is the violation of personal space. Privacy is a basic human right that combines the processing of personal data, personal communications by mail and the Internet, the processing of personal profiles on social media, forums, and other common environments. The new situation in the digital world changes the traditional understanding of private life as “the right to be alone” and introduces the new paradigm “the right to be forgotten”. For this reason, the provision of various information resources and the dissemination of information services via the Internet requires the creation of knowledge in society about the principles, methods, and technological means for adequate data processing. Many information security issues in the network spice can be directed to the privacy because different components of the digital world allow access and use of personal information.
Most social applications collect personal data outside the determined purpose, and this requires a serious risk analysis in their privacy policy. An example is the results of various surveys, which show that 74% of respondents consider the disclosure of personal data are an integral part of today’s digital world, 61% of users of social networks and sharing sites identify access to online services as the most important reason for disclosing personal data, and only 26% of social network users and 18% of online shoppers accept that they have full access to their personal data. It is known that not all personal data collected in social communications are provided directly by users, although 54% of them believe that they are informed about the conditions for collecting personal data and their subsequent use when joining a social networking site or register for an online service. Below is a systematization of the categories of personal data that are collected in the management of social communications and access to online services, divided into two main areas.
1. Information provided by the persons upon registration or
updating of a user profile:
• Personal identification data (names, pseudonym, address,
date of birth);
• Data with contact information (e-mail address, phone /
fax number, and country);
• Profile login information (input ID, password, other
security codes);
• Provided images and / or videos for user identification
(photos uploaded to the profile or provided in another way);
• Financial data (for credit cards or bank accounts);
• Other information provided by the user (reviews,
opinions, ratings, comments, interests, etc.).
2. Information Collected Automatically:
• Data about the device used (hardware model, identification
number and type of device, other unique identifiers, MAC
address, version of the operating system, software used, etc.);
• Location data (location by IP address or through other
location technologies, traffic data);
• Information about the visits (date and time of access,
duration of use, type of browser, pages viewed, type of browser,
blog and other used communication data and resources);
• Information about correspondence with the site
administrator;
• Information about the user from other sources (published
materials, other public information, information from other
social media, etc.).
To work in an online environment, users need to have a sufficiently high level of digital literacy, which includes knowledge of remote access and use of information resources (information literacy), knowledge of basic technological features in network communications (technological literacy) and information on the requirements for information security and protection of privacy (security literacy). Recently, there has been a slight increase in consumer literacy, rethinking the provision of sensitive personal data with a clear awareness that online privacy may be violated on social networks. In a sociological survey conducted in Germany, 84% of respondents answered that in the network space most personal data is required in social networks and communication service platforms, and 72% of them fear that they provide too much personal data and do not have complete control over them. Social networks provide a variety of personal information available to a wider range of people, which can lead to unwanted consequences (financial, psychological, reputation). Thus, they can become a tool that generates risk, unless you know the requirements for social online communication and compliance with certain rules. Some of them related to the latest provisions of the General Data Protection Regulation (GDPR) can be summarized as follows.
1. The main problem for user’s privacy in social networks
is that it is not clear who owns the published personal data -
the user or the owner of the site. This raises reasonable doubts
about the correct application of privacy policies related to the
question of how and for how long personal data is stored from
accounts, whether all account data is guaranteed to be deleted
at the end of the purpose (end of service use), whether deleted
and made copies of this data, etc.
2. The maintenance of a site requires the information
published on it to be correct, reliable and to take the necessary
organizational and technological measures for protection. This
is the responsibility of the site owner, who must have registered
as a Data Controller or is recognized as such (an obligation
under the GDPR), but if this is not done, the search for rights by
citizens is almost impossible. Moreover, if the so-called owner
is somewhere in the global network.
3. The basic requirement for lawful and correct processing
of personal data could hardly be applied to users of social
networks, assuming that they act as a Data Controller for
their own data and monitoring the implementation of this
requirement is very difficult.
4. According to the legal framework for data protection, the
information provided must be sufficient and relevant to the
defined goal, which, however, raises the following questions:
How can a specific social media goal for sharing any type of
information be defined and what is “sufficient information”?
Can personal information provided by one user be defined as
sufficient / insufficient for another user in the media?
5. Another legal requirement is that when providing
personal data, the consent of the person who is the owner of his
data (Data Subject) is required. The registration and creation
of a profile can be considered as consent of the person, but
whether this is in line with his requirement for restriction of
data categories (see above) and for regulated provision of data
from the profile for a certain group, which is not necessarily
involve third parties such as employers and other person of the
general society. How can this be controlled?
6. Users of social networks must pay due attention to user’s
ethics by publishing correct information. Removing (deleting)
problematic and incorrect content can be considered as
performing a censorship function.
7. The GDPR introduces the rule “the right to be forgotten”,
i.e. in case of refusal of a service, all personal data collected
during registration or provided by the respective user must be
deleted by the site maintainer. This is a major problem because
different copies of the data can be stored in different nodes
of the SNS (Social Networking Sites), which complicates the
deletion process.
8. The GDPR also requires the Data Controller to prove that
specific data must be retained, instead of the user proving
that its collection and storage is not necessary. Online service
providers must respect the principle of “default privacy”, which
means that the default settings must provide the required level
of privacy.
Conclusion
A precautionary measure in the protection of privacy should be the awareness that the provision of excessive personal information in the SoC can lead to various threats, including prosecution and harassment. The reasonable questions arise: “How to determine who is a Data controller?”; “When are the data protection regulations in social communications applied?”; “What is the appropriate law enforcement mechanism for social media?”; “When do exceptions occur?” Another view of the problem discussed in this article is presented in [12]. If someone chooses to participate in more than one social network, but wants to be identified as the same person, the chances of providing a lot of information about themselves are huge. Such participation reveals the location and schedule of users, which can lead to risk and it is important for people to learn how to manage their online data. The wide possibilities for access to personal data are in the pre-settings made, which act by default for each user - with one “click” you can accept the user conditions without actually knowing what they allow in their accounts. Even with a single visit to the page of a media, the user’s data is automatically saved and transferred to the corresponding center. Indicative in this respect is an example presented on the Internet: A law student requested to be provided with all the information that a social network has stored about him. As a result, he received 1,224 pages, including his photos, messages, and publications from years ago, some of which he considered deleted. A basic recommendation for social networks is to be extremely accurate and clear about what information they require so that users can decide whether to use the service. It is advisable to introduce notifications in case of violation of the use of personal data so that users can make the right choice.
References
- Kulishev N Theory and practice of social communications. p. 80.
- IGI Global What is Informatization.
- Sterley TL, JS Bains (2021) Social communication of affective states. Current Opinion in Neurobiology 68: 44-51.
- Bavel JJV, K Baicker, PS Boggio (2020) Using social and behavioural science to support COVID-19 pandemic response. Nature Human Behaviour 4: 460-471.
- Lizarralde I, Cr Mateos, Al Zunino, TA Majchrzak, TM Grønli (2020) Discovering web services in social web service repositories using deep variational autoencoders. Information Processing & Management 57(4): 102231.
- Pasi G, M Viviani (2020) Information credibility in social web: Contexts, approaches, and open issues. Presented at Italian Conference on Cybersecurity (ITASEC).
- Syran S, V Pattanaik, D Draheim (2020) Frameworks for collective intelligence: A systematic literature review. ACM Computing Surveys 53(1).
- Morais Storz (2020) Innovation and the role of problem formulation: Capitalizing on the potential of collective intellect for value creation. Chapter 15 in book “The Crest of the Innovation Management Research Wave” ((Edn.,). Marcus Tynnhammar), pp. 290.
- Kosmas P, G Galanakis, V Constantinou, Giannis Drossis, Maria Christofi, et al. (2020) Enhancing accessibility in cultural heritage environments: Considerations for social computing. Universal Access in Information Society 19: 471-482.
- Evans J (2020) Social Computing Unhinged. Journal of Social Computing 1(1): 1-13.
- Gribanova E, Al Savitsky (2020) Algorithm for estimating the time of posting messages on Vkontakte online social network. International Journal on Information Technologies and Security 12(1): 3-14.
- Romansky R (2014) Social Media and Personal Data Protection. International Journal on Information Technologies and Security 6(4): 65-80.

 Review Article
Review Article